
Raccoon is an offensive security tool known for reconnaissance and information gathering. The tool can extract useful information about the target host, such as DNS details, DNS mapping, WHOIS record, Port Scanning, TLS data (TLS version, supported ciphers, certificates), URL fuzzing, subdomains enumeration, and Web Application Firewall (WAF) information. Moreover, the tool is capable of fetching useful information from websites, such as web server information, CMS information, available HTML forms, email addresses, enumeration of sensitive files, cookies, robots.txt, and sitemap information.
Raccoon Installation
Raccoon is a Python tool that requires Python 3.5+ to operate. There are two methods available to install Raccoon scanner in Linux. The first method is the cloning of the Github repository using the following commands.
git clone https://github.com/evyatarmeged/Raccoon.git cd Raccoon python raccoon_src/main.py
The alternate method to install Raccoon scanner is by typing the following command in the terminal.
pip3 install raccoon-scanner
If the OS does not recognize pip3, the pip3 can be installed using the following command.
Sudo apt-get install python3-pip
Raccoon Scanning
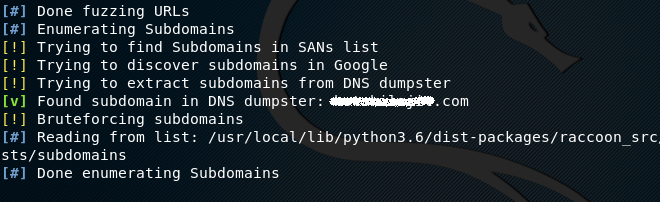
After successful installation of Raccoon, the tool can be set into action using the following command.
raccoon <options> <target>
There are multiple options available to gather the information about the target. All the available options can be explored by typing the ‘reccoon –help’ command. For demonstration purpose, we choose the –t (or –target) option to scan the target host to gather handful information. The command can be written as follows.
raccoon –t <target website>
The tool first detects the application protocol whether it is HTTP or HTTPS. The next task is to collect the DNS, TLS, and WAF information about the target.
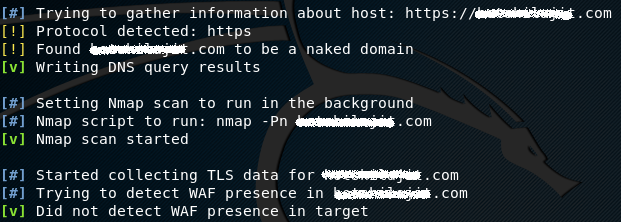
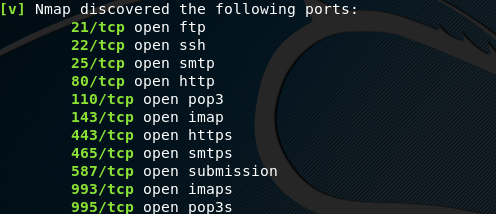
Port scanning is one of the important steps of reconnaissance. The tool uses the nmap utility to find open ports on the target host.
Apart from information gathering, Raccoon also gives vulnerability details based on the gathered information. For instance, the tool detects that the server may be vulnerable to Heartbleed.
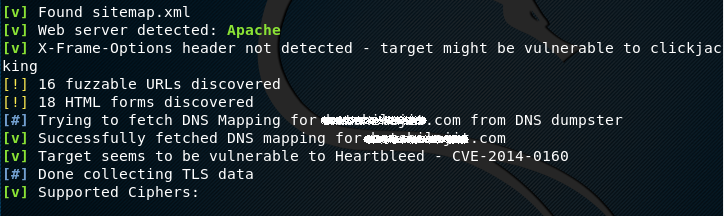
In future the developers are working to add an OWASP vulnerabilities scanning feature into the tool.
What Bunny rating does it get?
Information gathered by Raccoon is very useful in determining the possibility of some common vulnerabilities. The scan results are saved in files that can be used for future audits, analysis, and comparisons, as a result we will be awarding this tool a rating of 3.5 out of 5 bunnies.



Want to learn more about ethical hacking?
Do you know of another GitHub related hacking tool?
Get in touch with us via the contact form if you would like us to look at any other GitHub ethical hacking tools.


0 comments:
Post a Comment