Skip to content
 The advent of the Covid-19 pandemic and the impact on our society has resulted in many dramatic changes to how people are traveling, interacting with each other, and collaborating at work.There are several trends taking place as a consequence of the outbreak, which has only continued to heighten the need for the tightest possible cybersecurity.
The advent of the Covid-19 pandemic and the impact on our society has resulted in many dramatic changes to how people are traveling, interacting with each other, and collaborating at work.There are several trends taking place as a consequence of the outbreak, which has only continued to heighten the need for the tightest possible cybersecurity.
Tools for Collaboration
There has been a massive spike in the adoption of Tools for Collaboration as a consequence of COVID-19.Concerns about the coronavirus have caused an enormous increase in remote working, with many organizations requiring or at least encouraging their workers to stay at home—especially when cities, states, and even some entire nations are ultimately into lock down in a bid to spread the stem of the disease.Meanwhile, with millions working from home for many weeks now, there has been a spike in the video conferencing and online collaboration software, many of which are fortunately entirely free, allowing organizations to integrate them with their internal apps for better performance.Working from home can initially be a bit of the challenge. But it's also true that many organizations that have previously been reluctant to adopt remote working as a practice have now had little option but to embrace it.
There have been long many misconceptions in regards to remote working, but the worldwide pandemic has resulted in universal adoption of the practice that has forced previously dubious managers and executives to realize that remote working can actually have a massively positive impact on employee productivity, mental health, the environment, work-life balance, and expenses.As a result, many organizations have already started planning to incorporate flexible and remote working models into their schedules on a more permanent basis—even after the Covid-19 crisis is over.According to recent research published by global research and advisory company Gartner, the work culture move could be permanent for nearly half the workforce.
Remote working applications
Apparently, the number of applications needed to enable more remote working—especially on a more permanent basis—is clearly going to increase, and so will the number of customers and partners focused on Internet-facing applications.
Therefore, the availability and criticality of these applications will be extremely crucial for the future sustainability of the remote working practice, as well as enable businesses to collaborate and share information with their stakeholders, something that is only going to grow in importance.Because there is inevitably going to be a massive spike in internet-facing applications that will be of vital importance for such businesses, there will be an even greater focus on ensuring security is tight enough to make certain business continuity.
The Increasing Importance of Cybersecurity
Many serious businesses have already long-held cybersecurity as one of the most important issues that they face in the modern age, but with the increasing importance of remote working, it is only going to become an even more integral aspect of the future planning process for companies.
Having the best cybersecurity in place will allow quickly launching of a higher number of applications, ensuring that a business is better placed to cope not only with the current Covid-19 crisis but also to ensure the sustainability of future behavior after the pandemic has run its course.There are several essential verticals that businesses will need to learn to cope with as quickly as possible due to many factors resulting from Covid-19, including:
- the need for government to provide consumers more digital services,
- the quick adoption of remote learning by the education sector, and
- the need for the health system to develop innovative methods to deal with capacity problems.
The Solution
The solution to these problems will be greater collaboration and digitization and the embracing of focused consumer apps within these sectors.Cybersecurity needs to be seen as a method to quickly achieve these goals without any compromises to safety or the benefits that it is actually intended to deliver.
How to Approach the Cybersecurity Issue
Several things need to be provided by any approach to cybersecurity, including:
- Making exploitable risks to applications visible regularly.
- Providing businesses with the capability of mitigating such risks in real-time to ensure business continuity is maintained, given that a breach can have severe costs besides transactional and brand loss, including a loss of productivity when teams rely on such applications to successfully complete their work.
- Partnering with sector experts and businesses that provide these services, with the increase in demand, is likely to result in faster innovation that will make adoption more straightforward for companies without the need to create in-house expertise.
- Approach Cybersecurity as an enabler for businesses, allowing organizations to be more agile, faster, and fearless being digital while mitigating the continuity risks.
Several services, including the Indusface app known as AppTrana, provide fully managed application security that allows businesses to move faster and remain sustainable during and after the Covid-19 crisis.
 Today, cybersecurity researchers shed light on an Iranian cyber espionage campaign directed against critical infrastructures in Kuwait and Saudi Arabia.Bitdefender said the intelligence-gathering operations were conducted by Chafer APT (also known as APT39 or Remix Kitten), a threat actor known for its attacks on telecommunication and travel industries in the Middle East to collect personal information that serves the country's geopolitical interests."Victims of the analyzed campaigns fit into the pattern preferred by this actor, such as air transport and government sectors in the Middle East," the researchers said in a report (PDF) shared with The Hacker News, adding at least one of the attacks went undiscovered for more than a year and a half since 2018."The campaigns were based on several tools, including 'living off the land' tools, which makes attribution difficult, as well as different hacking tools and a custom-built backdoor."
Today, cybersecurity researchers shed light on an Iranian cyber espionage campaign directed against critical infrastructures in Kuwait and Saudi Arabia.Bitdefender said the intelligence-gathering operations were conducted by Chafer APT (also known as APT39 or Remix Kitten), a threat actor known for its attacks on telecommunication and travel industries in the Middle East to collect personal information that serves the country's geopolitical interests."Victims of the analyzed campaigns fit into the pattern preferred by this actor, such as air transport and government sectors in the Middle East," the researchers said in a report (PDF) shared with The Hacker News, adding at least one of the attacks went undiscovered for more than a year and a half since 2018."The campaigns were based on several tools, including 'living off the land' tools, which makes attribution difficult, as well as different hacking tools and a custom-built backdoor."
Known to be active since 2014, the Chafer APT has previously taken aim at Turkish government organizations and foreign diplomatic entities based in Iran with the goal of exfiltrating sensitive data.A FireEye report last year added to growing evidence of Chafer's focus on telecommunications and travel industries. "Telecommunications firms are attractive targets given that they store large amounts of personal and customer information, provide access to critical infrastructure used for communications, and enable access to a wide range of potential targets across multiple verticals," the company said.APT39 compromises its targets via spear-phishing emails with malicious attachments and using a variety of backdoor tools to gain a foothold, elevate their privileges, conduct internal reconnaissance, and establish persistence in the victim environment.What makes the Kuwait attack more elaborate, according to Bitdefender, is their ability to create a user account on the victims' machine and perform malicious actions inside the network, including network scanning (CrackMapExec), credential harvesting (Mimikatz), and move laterally inside the networks using a wide arsenal of tools at their disposal.Most activity occurs on Friday and Saturday, coinciding with the weekend in the Middle East, the researchers said.The attack against a Saudi Arabian entity, on the other hand, involved the use of social engineering to trick the victim into running a remote administration tool (RAT), with some of its components sharing similarities with those used against Kuwait and Turkey.
"While this attack was not as extensive as the one in Kuwait, some forensic evidence suggests that the same attackers might have orchestrated it," the researchers said. "Despite the evidence for network discovery, we were not able to find any traces for lateral movement, most probably because threat actors were not able to find any vulnerable machines."The attacks against Kuwait and Saudi Arabia are a reminder that Iran's cyber espionage efforts have shown no sign of slowing down. Given the crucial nature of the industries involved, Chafer's actions continue the trend of striking countries that act against its national ambitions."While these two are the most recent attack examples happening in the Middle East, it is important to understand that this type of attack can happen anywhere in the world, and critical infrastructures like government and air transportation remain very sensitive targets," Bitdefender said.
 As cyberattacks continue to proliferate in volume and increase in sophistication, many organizations acknowledge that some part of their breach protection must be outsourced, introducing a million-dollar question of what type of service to choose form.Today, Cynet releases the Security Outsourcing Guide (download here), providing IT Security executives with clear and actionable guidance on the pros and cons of each outsourcing alternative.The reason for security outsourcing increasing momentum is that unlike traditional IT, cyber threats evolve at a much faster pace.While relatively not long ago, AV and firewall covered most of the standard organization's cybersecurity needs, today no security posture can be considered complete without a certain level of incident response capabilities, alert prioritization, root cause analysis and forensic investigation – and security professional that are sufficiently qualified in this domain both are hard to find as well as costly to retain.But the challenge is not only in manning an active breach of emergency mode style positions. Even the ongoing operation and day to day management of monitoring and detection products is not trivial.Discerning between an alert that indicated a potential systemic risk and an alert triggered by a minor IT misconfiguration is far from trivial, and the challenge intensifies when recalling that many small and mid-sized organizations rely on their IT staff to part-time manage their cybersecurity without a dedicated team in place.In fact, even the most initial setup of the security stack introduces potential difficulties. What products or technologies should be prioritized as core components? Would it be EDR or Email Protection? Is monitoring user activities on cloud apps more important than protection from fileless malware?The fact is that the lack of textbook answers to such questions is a problem for many security decision-makers, making it a small wonder that numerous outsource alternatives are offered today by MSSP, Systems Integrators, IT Service Providers, and MDRs.The Security Outsourcing Guide walks its reader through the wide range of outsourcing alternatives, as well as points out the unique characteristics that would make a certain organization a better fit for each.The Companion divides security outsourcing to three families:
As cyberattacks continue to proliferate in volume and increase in sophistication, many organizations acknowledge that some part of their breach protection must be outsourced, introducing a million-dollar question of what type of service to choose form.Today, Cynet releases the Security Outsourcing Guide (download here), providing IT Security executives with clear and actionable guidance on the pros and cons of each outsourcing alternative.The reason for security outsourcing increasing momentum is that unlike traditional IT, cyber threats evolve at a much faster pace.While relatively not long ago, AV and firewall covered most of the standard organization's cybersecurity needs, today no security posture can be considered complete without a certain level of incident response capabilities, alert prioritization, root cause analysis and forensic investigation – and security professional that are sufficiently qualified in this domain both are hard to find as well as costly to retain.But the challenge is not only in manning an active breach of emergency mode style positions. Even the ongoing operation and day to day management of monitoring and detection products is not trivial.Discerning between an alert that indicated a potential systemic risk and an alert triggered by a minor IT misconfiguration is far from trivial, and the challenge intensifies when recalling that many small and mid-sized organizations rely on their IT staff to part-time manage their cybersecurity without a dedicated team in place.In fact, even the most initial setup of the security stack introduces potential difficulties. What products or technologies should be prioritized as core components? Would it be EDR or Email Protection? Is monitoring user activities on cloud apps more important than protection from fileless malware?The fact is that the lack of textbook answers to such questions is a problem for many security decision-makers, making it a small wonder that numerous outsource alternatives are offered today by MSSP, Systems Integrators, IT Service Providers, and MDRs.The Security Outsourcing Guide walks its reader through the wide range of outsourcing alternatives, as well as points out the unique characteristics that would make a certain organization a better fit for each.The Companion divides security outsourcing to three families:
- IR Oriented: this family includes outsourcing only IR related activities and features a wide range of variance from mere monitoring and notification through remote assistance and guidance to full forensic investigation and remediation activities. In terms of business models, it could be retainer-based or on-demand, Typical service providers of these families are MSSP and MDR.
- Ongoing Management Oriented: this family applies to organizations that would rather that even the continuous operation of their prevention and detection technologies will be carried out by a more skilled team and is mostly found among organizations with little security expertise and without a dedicated security team. Here, as well, there are various flavors that can range from management of just the more advanced detection and monitoring tools to full management of the entire security stack. Typical service providers of these families are MSSP, MDR, and MSP.
- Design and Set-Up Oriented: that's the widest family in terms of outsourced functionalities and includes end-to-end outsourcing of the decision what product to choose and install, how to integrate them together, and which threats should be prioritized in terms in what products to invest. Typical service providers of these families are MSSP, MSP, and System Integrators.
In addition, the guide dedicates a chapter to the more common role of the Virtual CISO or vCISO – an individual that has typically gained a rich security background holding positions at organizations with mature security posture and has thus acquired significant knowledge on cyber technologies and services. As a result, he\she is in an optimal position to advise less mature organizations – often without a CISO themselves how to tailor the best fit security for their needs.Download the Security Outsource Options Guide here.
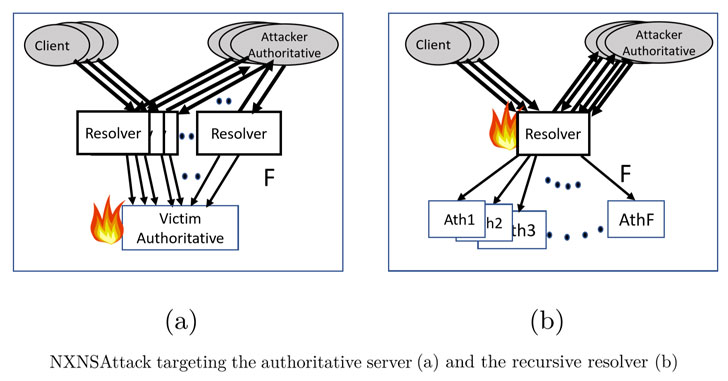
 Israeli cybersecurity researchers have disclosed details about a new flaw impacting DNS protocol that can be exploited to launch amplified, large-scale distributed denial-of-service (DDoS) attacks to takedown targeted websites.Called NXNSAttack, the flaw hinges on the DNS delegation mechanism to force DNS resolvers to generate more DNS queries to authoritative servers of attacker's choice, potentially causing a botnet-scale disruption to online services."We show that the number of DNS messages exchanged in a typical resolution process might be much higher in practice than what is expected in theory, mainly due to a proactive resolution of name-servers' IP addresses," the researchers said in the paper."We show how this inefficiency becomes a bottleneck and might be used to mount a devastating attack against either or both, recursive resolvers and authoritative servers."Following responsible disclosure of NXNSAttack, several of the companies in charge of the internet infrastructure, including PowerDNS (CVE-2020-10995), CZ.NIC (CVE-2020-12667), Cloudflare, Google, Amazon, Microsoft, Oracle-owned Dyn, Verisign, and IBM Quad9, have patched their software to address the problem.
Israeli cybersecurity researchers have disclosed details about a new flaw impacting DNS protocol that can be exploited to launch amplified, large-scale distributed denial-of-service (DDoS) attacks to takedown targeted websites.Called NXNSAttack, the flaw hinges on the DNS delegation mechanism to force DNS resolvers to generate more DNS queries to authoritative servers of attacker's choice, potentially causing a botnet-scale disruption to online services."We show that the number of DNS messages exchanged in a typical resolution process might be much higher in practice than what is expected in theory, mainly due to a proactive resolution of name-servers' IP addresses," the researchers said in the paper."We show how this inefficiency becomes a bottleneck and might be used to mount a devastating attack against either or both, recursive resolvers and authoritative servers."Following responsible disclosure of NXNSAttack, several of the companies in charge of the internet infrastructure, including PowerDNS (CVE-2020-10995), CZ.NIC (CVE-2020-12667), Cloudflare, Google, Amazon, Microsoft, Oracle-owned Dyn, Verisign, and IBM Quad9, have patched their software to address the problem.
The DNS infrastructure has been previously at the receiving end of a rash of DDoS attacks through the infamous Mirai botnet, including those against Dyn DNS service in 2016, crippling some of the world's biggest sites, including Twitter, Netflix, Amazon, and Spotify.
The NXNSAttack Method
A recursive DNS lookup happens when a DNS server communicates with multiple authoritative DNS servers in a hierarchical sequence to locate an IP address associated with a domain (e.g., www.google.com) and return it to the client.This resolution typically starts with the DNS resolver controlled by your ISPs or public DNS servers, like Cloudflare (1.1.1.1) or Google (8.8.8.8), whichever is configured with your system.The resolver passes the request to an authoritative DNS name server if it's unable to locate the IP address for a given domain name.But if the first authoritative DNS name server also doesn't hold the desired records, it returns the delegation message with addresses to the next authoritative servers to which DNS resolver can query.
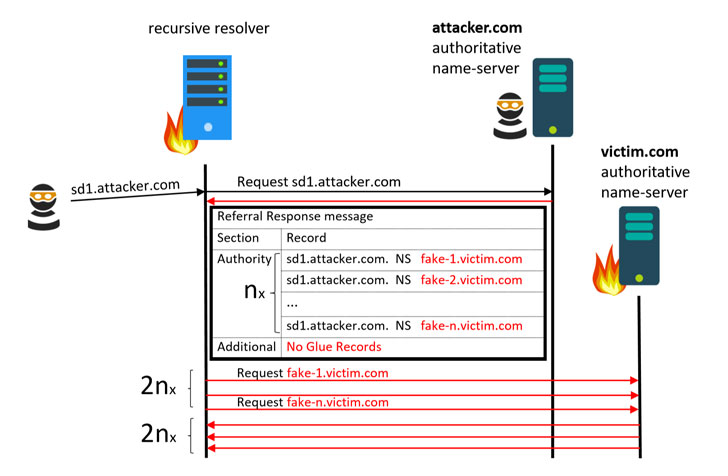
In other words, an authoritative server tells the recursive resolver: "I do not know the answer, go and query these and these name servers, e.g., ns1, ns2, etc., instead".This hierarchical process goes on until the DNS resolver reaches the correct authoritative server that provides the domain's IP address, allowing the user to access the desired website.Researchers found that these large undesired overheads can be exploited to trick recursive resolvers into forcefully continuously sending a large number of packets to a targeted domain instead of legitimate authoritative servers.In order to mount the attack through a recursive resolver, the attacker must be in possession of an authoritative server, the researchers said."This can be easily achieved by buying a domain name. An adversary who acts as an authoritative server can craft any NS referral response as an answer to different DNS queries," the researchers said.The NXNSAttack works by sending a request for an attacker-controlled domain (e.g., "attacker.com") to a vulnerable DNS resolving server, which would forward the DNS query to the attacker-controlled authoritative server.Instead of returning addresses to the actual authoritative servers, the attacker-controlled authoritative server responds to the DNS query with a list of fake server names or subdomains controlled by the threat actor that points to a victim DNS domain.
The DNS server, then, forwards the query to all the nonexistent subdomains, creating a massive surge in traffic to the victim site.The researchers said the attack can amplify the number of packets exchanged by the recursive resolver by as much as a factor of more than 1,620, thereby overwhelming not only the DNS resolvers with more requests they can handle, but also flood the target domain with superfluous requests and take it down.
What's more, using a botnet such as the Mirai as a DNS client can further augment the scale of the attack."Controlling and acquiring a huge number of clients and a large number of authoritative NSs by an attacker is easy and cheap in practice," the researchers said."Our initial goal was to investigate the efficiency of recursive resolvers and their behavior under different attacks, and we ended up finding a new seriously looking vulnerability, the NXNSAttack," the researchers concluded."The key ingredients of the new attack are (i) the ease with which one can own or control an authoritative name server, and (ii) the usage of nonexistent domain names for name servers and (iii) the extra redundancy placed in the DNS structure to achieve fault tolerance and fast response time," they added.It's highly recommended that network administrators who run their own DNS servers update their DNS resolver software to the latest version.